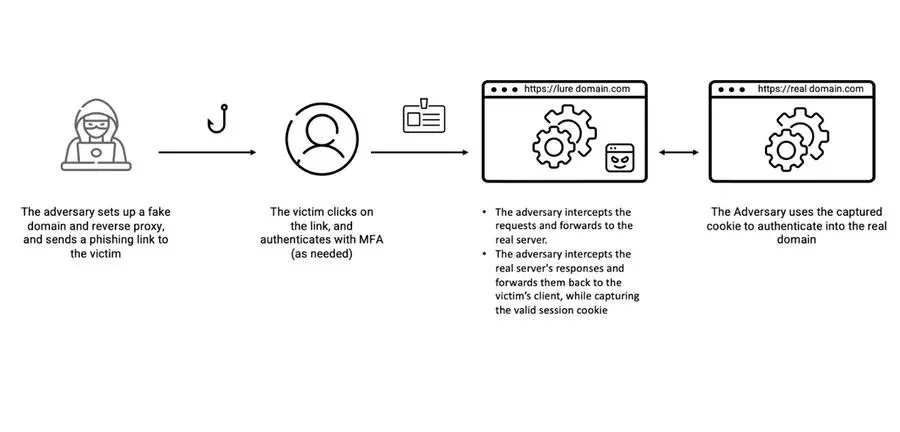

- EvilProxy - a phishing tool based on a reverse proxy architecture, was used, which allows attackers to steal MFA-protected credentials and session cookies.
Dubai, UAE: Proofpoint research has revealed that at least 35% of all account takeover attacks over the past year had multifactor authentication (MFA) enabled. Threat actors are continuing to advance their methods for account takeovers, so they can steal data, deliver malware, or use the account’s access and permissions for malicious purposes. Though MFA is a step up from password-only authentication and its use has increased over the past few years in organizations, it has not stopped security breaches.
Proofpoint researchers have revealed that attackers now use new advanced automation to accurately determine in real-time whether a phished user is a high-level profile. They immediately focus on taking over that account, while ignoring less lucrative phished profiles.
Driven by open-source kits, threat actors have created MFA Phishing as a Service (PhaaS), enabling access to pre-configured kits for online services such as Gmail, Microsoft, Dropbox, Facebook, and X/ Twitter. Attackers can easily launch campaigns using a point-and-click interface with customizable options, such as bot detection, proxy detection, and geofencing. This relatively simple and low-cost interface has led to a surge in MFA phishing.
One such interface and toolkit is EvilProxy, an all-inclusive phishing kit that is easy to acquire, configure, and set up. Proofpoint threat analysts have identified a concerning gap in public awareness regarding the risks and potential harm of EvilProxy.
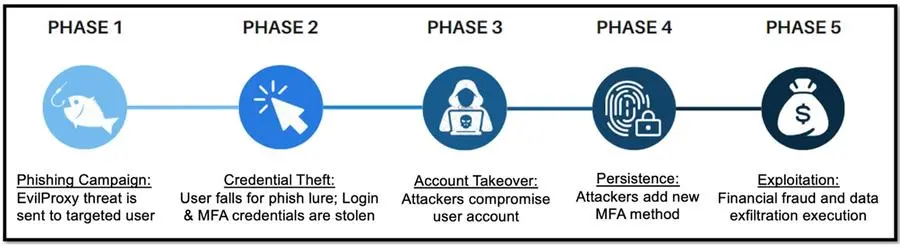
Since early March, Proofpoint researchers have monitored an ongoing hybrid campaign using EvilProxy to target thousands of Microsoft 365 user accounts. Approximately 120,000 phishing emails were sent to hundreds of targeted organizations across the globe between March and June 2023.
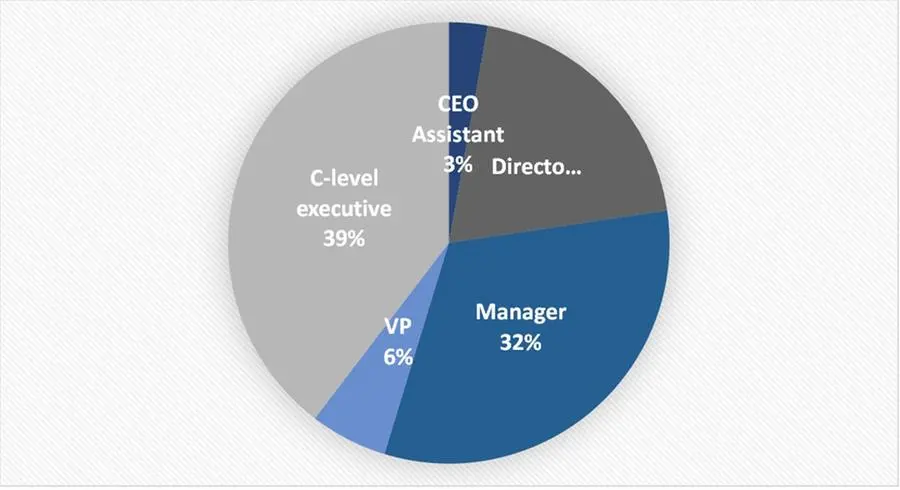
Targeted users included many high-value targets, such as C-level executives & VPs at leading companies, especially valued by threat actors due to their potential access to sensitive data and financial assets. Amongst the hundreds of compromised users, approximately 39% were C-level executives of which 17% were Chief Financial Officers, and 9% were Presidents and CEOs. Attackers have also shown interest in lower-level management, focusing their efforts on personnel with access to financial assets or sensitive information.
During the phishing stage of the attack, attackers employed techniques such as:
- Brand impersonation – Sender addresses impersonated trusted services and apps, such as Concur Solutions, DocuSign and Adobe.
- Scan blocking – Attackers utilized protection against cyber security scanning bots, making it harder for security solutions to analyze their malicious web pages.
- Multi-step infection chain – Attackers redirected traffic via open legitimate redirectors, including YouTube, followed by additional steps, such as malicious cookies and 404 redirects.
Reverse proxy threats like EvilProxy are a potent threat in today’s evolving landscape, surpassing older, less capable phish kits. They have risen significantly in popularity and exposed crucial gaps in organizations’ defense strategies. For that reason, attackers are quickly pivoting to easy-to-use advanced phishing kits, which leads to an increase in hybrid attacks’ efficacy and velocity. While these attacks start with email, their final goal is to compromise and exploit valuable cloud user accounts, assets, and data. This concern is echoed in the UAE, where email fraud tops the list of the most significant threats according to Proofpoint Voice of the CISO 2023.

Cybercriminals employ various techniques, including lateral movement and malware proliferation. Attackers study their target organizations’ culture, hierarchy, and processes, to prepare their attacks and improve success rates. Attackers have executed financial fraud, performed data exfiltration or done Hacking-as-a-Service (HaaS) transactions, selling access to compromised user accounts.
Recommendations
Organizations can protect themselves against advanced hybrid (email-cloud) threats through the following methods:
Email Security: Block and monitor malicious email threats targeting your users.
Effective BEC-prevention solutions can greatly minimize practical attack surfaces.
Cloud Security: Identify account takeover (ATO) and unauthorized access to sensitive resources within your cloud environment. These solutions should provide accurate and timely detection of both the initial account compromise and post-compromise activities, including visibility into abused services and applications. Auto-remediation capabilities to reduce attackers’ dwell time and potential damages.

Web Security: Isolate potentially malicious sessions initiated by links embedded in email messages.
Security Awareness: Educate users to be aware of these risks when using Microsoft 365.
FIDO: Consider adopting FIDO-based physical security keys (https://fidoalliance.org/how-fido-works).



















