PHOTO
Positive Technologies, an industry leader in result-driven cybersecurity, has analyzed cyberthreats relevant to the financial sector.[1] Unique attacks on this industry doubled in Q3 2023 compared to the same period last year. Attackers primarily targeted the least secure organizations and their customers, most often with the help of malware. The percentage of encryption malware in such incidents increased 3.5 times. In addition, hackers are now more likely to exploit vulnerabilities on the network perimeter and compromise financial companies by attacking their supply chains. The databases and credentials obtained in such attacks are sold on cybercriminal platforms. At the same time, financial institutions continue to be targeted by hacktivists.
In the first nine months of 2023, most attacks (35%) involved malware. Encryption malware was used in 63% of incidents, while a year earlier it accounted for only 18%. The percentage of social engineering among the attack methods dropped from 47% to 25%. Positive Technologies attributes this to the growing popularity of other attack methods.
Analysts noticed a significant increase in incidents that exploited vulnerabilities on the network perimeter (32% of cases). There was also a significant percentage of incidents (22%) where organizations were compromised via their supply chains. Oftentimes, open-source software was used in such incidents to distribute malicious code. In one attack, the cybercriminals even created a fake LinkedIn page where they impersonated an employee of the targeted bank to conceal spoofing. Positive Technologies believes that such attacks may see a rise in popularity in the next few years, given the widespread use of open-source software by companies, including financial organizations, in their in-house software development projects.

Positive Technologies recommends that financial companies monitor the use of third-party components when developing their own software and check them for backdoors and vulnerabilities.
"Our research reveals that companies around the world have extremely low network perimeter security," Evgeny Gnedin, Head of Security Analytics at Positive Technologies, commented. "This was confirmed by penetration tests conducted by our experts for financial institutions in 2023. Our pentesters were able to gain access to corporate local area networks of all customer organizations by exploiting vulnerabilities in Internet-connected software. Only one bank tested had a good security system, but pentesters still managed to find and exploit a zero-day vulnerability. This proves that a motivated attacker can penetrate the IT infrastructure of even relatively well-protected banks. Therefore, financial companies need to build security systems that will prevent non-tolerable damage to their business even if a hacker launches a successful attack."
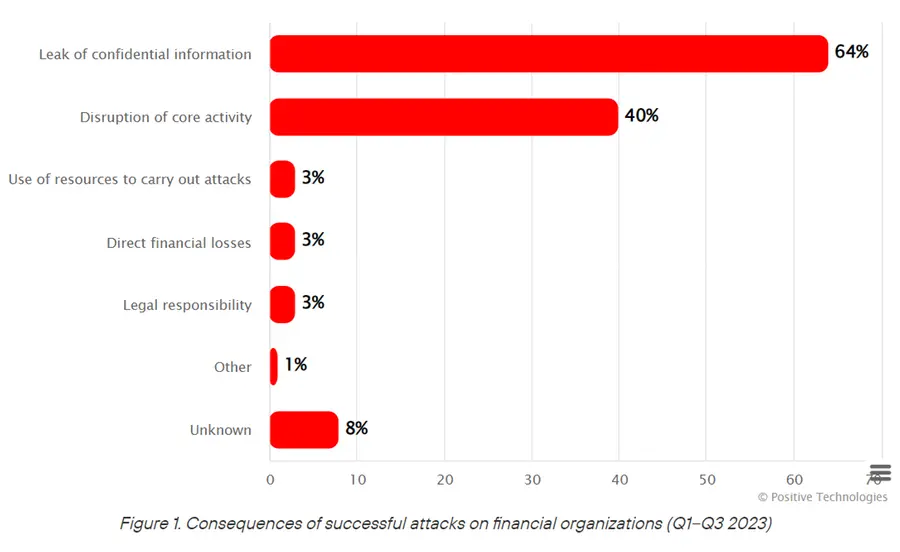
Data leaks continued to be the most common attack consequence, rising from 51% to 64%. Among all malicious ads in the dark web and on dedicated Telegram channels and chats,[2] database-related messages accounted for 42%. In 43% of them, files were distributed for free: this is how hackers tend to punish companies for refusing to pay ransom. Ads selling fresh data and insider services amounted to 30%. Half of the databases under analysis had a maximum price tag of one thousand dollars, with one data row selling for about five dollars. Messages of database buyers accounted for 29%. Positive Technologies explains this high percentage by the fact that attackers are targeting specific organizations. In the financial sector, targeted attacks account for 98% of all incidents.
About 40% of the incidents involved disruptions in the availability of financial services, mostly caused by ransomware attacks. This malware type was used in 63% of successful attacks. Some systems were shut down as a result of hacktivist attacks. Such incidents are typical for regions experiencing geopolitical tensions.
"Hacktivists attack individual companies, with the ultimate goal of destabilizing the country's entire financial system,'' said Artem Sychev, Advisor to CEO at Positive Technologies. "Attackers hope to spread panic among citizens and make them distrust financial institutions and the government. In this environment, financial companies should build their cybersecurity systems in such a way that prevents non-tolerable events from happening. This will ensure high operational reliability."
Mr. Sychev also highlighted the need for a centralized approach in addressing the growing cybersecurity challenges. This approach should include a coordinated response to threats at the industry level, as well as an analysis of possible chains of events that could lead to fatal consequences.
To mitigate cyber threats, the financial sector is recommended to use up-to-date security tools, such as solutions for monitoring cybersecurity events and detecting incidents (MaxPatrol SIEM), endpoint security systems that protect against sophisticated and targeted attacks, effective vulnerability detection and management tools (MaxPatrol VM), fully automated result-driven cybersecurity solutions, and sandboxes that offer flexible customization of virtual environments to facilitate analysis and detect threats in files and network traffic (PT Sandbox).
About:
Positive Technologies is an industry leader in result-driven cybersecurity and a major global provider of information security solutions. Our mission is to safeguard businesses and entire industries against cyberattacks and non-tolerable damage. Over 3,300 organizations worldwide use technologies and services developed by our company. Positive Technologies is the first and only cybersecurity company in Russia to have gone public on the Moscow Exchange (MOEX: POSI), with 170,000 shareholders and counting. Follow us in the News section at ptsecurity.com.
Media contact
Ziad Baig
Associate Communications Consultant
ziad@activedmc.com
[1]The study looks at the first three quarters of 2023. The analysis is based on research conducted by Positive Technologies, analytical reports from leading cybersecurity companies, and data from trusted news media that aggregate information on cyberincidents. It covers both banks and non-lending financial institutions (such as insurance companies, professional stock market players, or investment funds).
[2] During the study, Positive Technologies analyzed 236 Telegram channels and dark web forums, with a total of 16,734,680 users and 112,812,462 messages. These included the largest multilingual platforms centered around various subjects.




















