- They have moved their activities to online platforms during the pandemic, with minimal disruption, thanks to years of investment in infrastructure and systems.
- We believe GCC banks are managing their exposure to cyber risk effectively, including through investment in digital security, and that their strong profitability, capitalization, and liquidity provide a financial buffer against potential incidents.
Cyber risk is a mounting threat to the operations and credit profiles of financial institutions, and never more so than since the pandemic accelerated the shift to online banking. There have been no major interruptions to the operations of banks in GCC countries, however. For example, in Saudi Arabia, mortgage lending continued to expand at double-digit rates despite the digital shift. GCC banks laid the foundation for success over several years by investing in infrastructure and systems, including equipment and software, to minimize their exposure to cyber risk, while also benefiting from supportive regulatory frameworks and cyber risk requirements.
S&P Global Ratings believes GCC banks' exposure to cyber risk is manageable, assuming they continue to invest in cyber security and proactively manage risk, taking into consideration the evolving nature of threats. We note that GCC banks have reported only a handful of digital breaches and cyberattacks over the past decade. While some might have gone unreported, it is likely these were minor incidents given the absence of significant losses in financial reports and the banks' relatively low operational risk capital charges.
Our view of manageable cyber risk for GCC banks is supported by data from cyber security specialist Guidewire. It estimates that the region's top 19 banks (for which data was available) would suffer an average 7.5% fall in net income and a 0.6% decline in equity, based on figures from the end of 2021, under a high-severity cyber incident; at the same time, the banks' average operational risk capital charge was 3.6% of total equity. We believe the data suggests that GCC banks appear to have sufficient operational risk capital to cover losses related to cyber risk. We do not incorporate Guidewire's simulation in our capital analysis, though it provides us with insight that is useful as we consider risk management. We note that Guidewire doesn't incorporate the possible impact of a cyber incident on a bank's business position, associated revenue loss potential due to reputation damage, or cyber ransom. We consider those factors as part of our credit rating analysis.
How Cyber Risk Affects Our Analysis Of Banks
We incorporate banks' exposure to cyber risk in our assessment of their risk profile and management. Cyberattacks have the potential to harm banks' credit profiles through reputation damage as well as monetary loss. In the event of a large-scale attack on a systemic bank or several large institutions, we could foresee governments taking measures to stabilize the sector.
In our analysis of banks' creditworthiness, we consider the impact of cyber risks on the banking system as well as at individual banks. Our systemwide banking sector analysis captures cyber risks in a given country, when, for example, an entire banking industry suffered from a series of repeated, serious breaches of security, or regulators appear to be more reactive than proactive in forcing financial institutions to strengthen their cyber security frameworks.
Our analysis of bank-specific factors examines the implications of cybersecurity events for:
- Business position stability, which could be impaired by loss of customer confidence as a result of a successful attack. We also consider the ability to manage and prevent cyber risks as part of our management and governance assessment.
- Potential losses from cyber events, including the risk of material losses that could hurt a bank's capitalization.
- Risk management, where poorly managed cyber risks could expose structural weaknesses.
- Reputation damage, that could result from a severe cyber event, and in extreme cases, potentially lead to sudden outflows of clients' funds and liquidity pressure.
Continued Investment And Capitalization Help Minimize Cyber Risk
Exposure
Over the past decade, GCC banks have reported a small number of cyberattacks that resulted in monetary or reputational damage. In addition, the overall operational risk capital charge, which is part of the local capital requirements, stood at 3.4% of total equity at the end of 2021 (assuming an 8% minimum capital requirement ratio). Banks that are present in more than one country, and those that have significant retail operations, reported the highest charge within our sample of GCC banks. Given that cyber risk is one of the elements operational risk capital is designed to cover, the allocation suggests that GCC banks regard their cyber risk exposure as low.
GCC banks' low cyber risk exposure is underpinned by:
Significant investment in infrastructure, equipment, and software, including for cyber risk mitigation. Although GCC banks have not publicly disclosed figures for the investments, we understand from our interactions with rated banks that their boards of directors and senior management allocate significant attention to cyber risk. GCC banks have also invested in technology, equipment, and staff training to detect and limit exposure to cyber risk, and continue to update their policies and investments to factor emerging trends in the cyber security space. We recognize, however, that no system is perfect, and that continued investments and adaptation are required to minimize risk.
Local regulatory frameworks and requirements centered on cyber security. This includes the Saudi Central Bank's cyber security framework, issued in 2017, which defined requirements around governance, risk management, compliance, operations, technology, and the use of
third-party cyber security services by regulated entities. Those rules were supplemented, in 2022, with a document on cyber threat intelligence principles, which addressed the production and dissemination of intelligence aimed at identifying and minimizing cyber threats. The United Arab Emirates (UAE) Central Bank established, in late 2021, a Networking and Cyber Security
Operations Centre to better protect the local financial system against cyberattacks. The central bank has also identified and worked to improve key pillars of effective cyber resilience for the banking system and its own infrastructure. Moreover, the Central Bank of Qatar published a circular in 2018 that outlines the regulatory requirements banks must fulfill to effectively manage cyber risk.
Our belief that GCC banks can manage their exposure to potential negative credit effects from cyber risks is consistent with Guidewire's estimates.
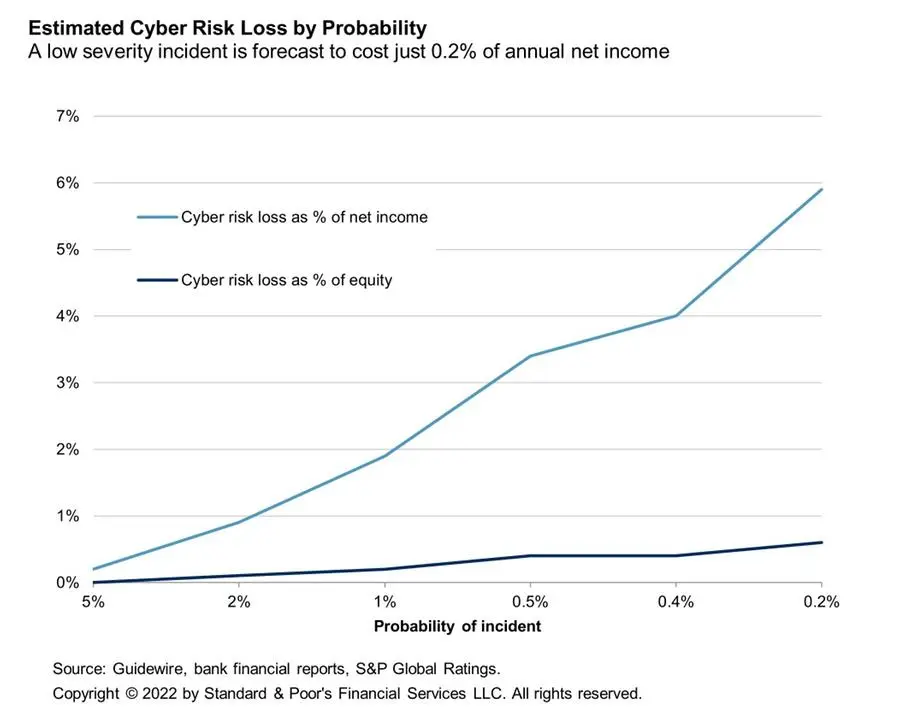
Using a tail-value-at-risk calculation that measures the average loss for the 40 most severe simulations in Guidewire's model, the top 19 banks in the GCC (for which data is available) would suffer an average loss of 8.3% of net income and 0.7% of equity following a high severity cyberattack, based on their financial position at the end of 2021. The simulations also indicate that, on average, banks with higher geographic diversification face greater risks, as do those with more extensive retail operations (see chart 1). Guidewire's projections indicate that a low severity incident (with 5% probability of occurring) would cost an average 0.2% of net income for the GCC banks in our sample (see chart 2).
Guidewire's calculations suggest that GCC bank's operational risk capital is sufficient. However, this assessment does not incorporate possible business position effects, associated revenue loss potential due to reputational damage, or cyber ransom. We also note that Guidewire's coverage of GCC banks excludes some smaller entities that could be relatively vulnerable to cyber risks.
We factor cyber risk into our assessment of banks' business stability, capitalization, and risk management adequacy. In extreme scenarios, cyber risk could have negative implications on liquidity through a sudden outflow of funds, leading to liquidity pressure. We also note that cyber risks evolve rapidly and require continued efforts if banks are to remain protected, and we recognize that no system can fully protect against unexpected-event risks.
CHART1
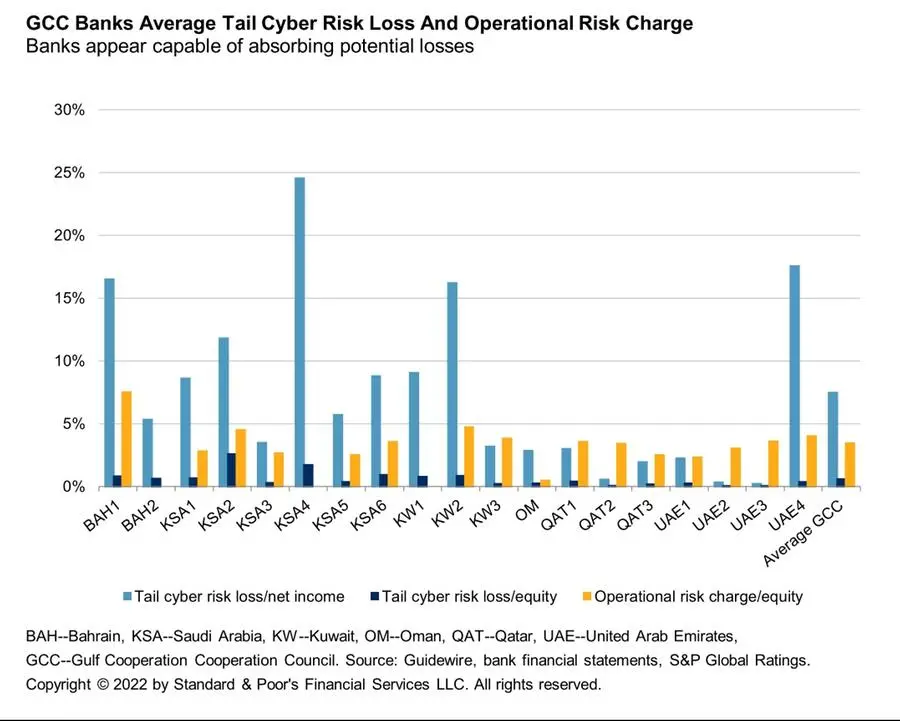

CHART2

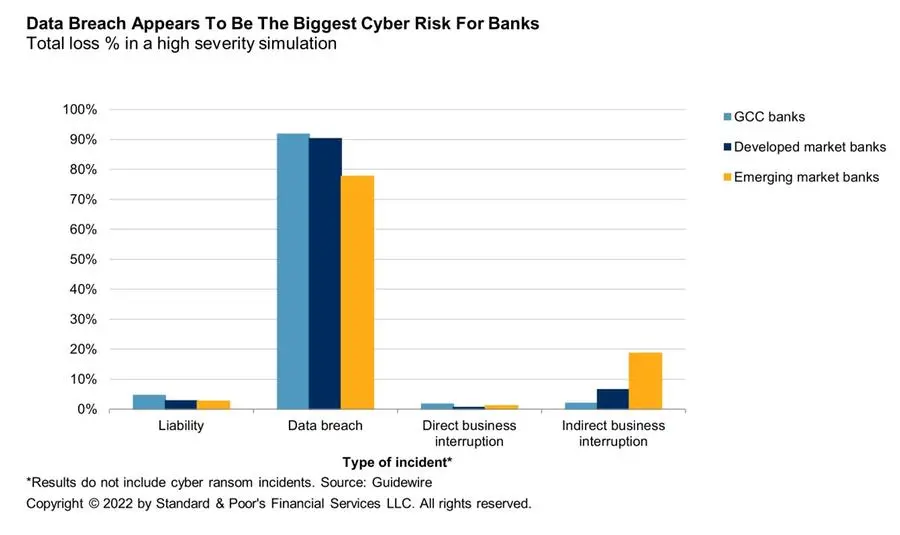
Data Breaches Are Among The Biggest Risks
Cyber risks range from a temporary interruption of services to the complete shutdown of IT systems due to data destruction and data theft linked to cyber ransoms. The growth of
ransomware linked to data theft, coupled with the significant amount of sensitive information handled by banks, suggest that this is a major risk for the GCC's lenders, particularly compared to other dangers such as business interruption. Ransomware-related attacks leading to data leaks increased by 82% in 2021 when there were 2,686 attacks, up from 1,474 over 2020, according to the "2022 Global Threat Report" from Crowdstrike, a cybersecurity technology company.
The risk of cyberattacks appears even higher for banks with greater geographic diversification (particularly those with operations in regions more prone to cyber-attacks than the GCC) and banks with extensive retail operations, which have proven more likely to attract the interest of hackers.
Guidewire's findings (see chart 3) suggest that the cyber risk profile of GCC banks is comparable to developed markets, rather than emerging market banks. It is notable that emerging markets are significantly more prone than the GCC to indirect business interruption issues, which stem from problems at third-party service providers. That could be explained by GCC countries' significant investment in infrastructure, which appears to have reduced indirect business interruption risks.
CHART3

Notable Cyber Incidents In GCC
Country Incident
- Qatar Hackers claimed to have gained access to the servers of a Qatari bank and leaked the personal data of its customers. Documents were subsequently posted to the whistleblower site Cryptome in April 2016. The leak comprised more than 15,000 files, including passwords, pin numbers, and payment card data.
- Saudi Arabia The website of a Saudi bank was reportedly taken down by a cyberattack in February 2015.
- Oman In February 2013, an Omani bank said that 12 of its credit cards were compromised in an alleged hack originating from outside Oman.
- Bahrain In October 2018, an attack on Pakistan's banking system resulted in the theft of details relating to more than 19,000 debit cards, including 25 cards issued by a Bahraini bank with operations in Pakistan.
Source:Guidewire
This report does not constitute a rating action.
-Ends-
Copyright © 2022 by Standard & Poor’s Financial Services LLC. All rights reserved.
STANDARD & POOR’S, S&P and RATINGSDIRECT are registered trademarks of Standard & Poor’s Financial Services LLC.
Disclaimer
S&P may receive compensation for its ratings and certain analyses, normally from issuers or underwriters of securities or from obligors.
S&P reserves the right to disseminate its opinions and analyses. S&P's public ratings and analyses are made available on its Web sites, www.standardandpoors.com (free of charge), and www.ratingsdirect.com (subscription), and may be distributed through other means, including via S&P publications and third-party redistributors. Additional information about our ratings fees is available at www.standardandpoors.com/usratingsfees.
S&P keeps certain activities of its business units separate from each other in order to preserve the independence and objectivity of their respective activities. As a result, certain business units of S&P may have information that is not available to other S&P business units. S&P has established policies and procedures to maintain the confidentiality of certain non-public information received in connection with each analytical process.
To the extent that regulatory authorities allow a rating agency to acknowledge in one jurisdiction a rating issued in another jurisdiction for certain regulatory purposes, S&P reserves the right to assign, withdraw or suspend such acknowledgment at any time and in its sole discretion. S&P Parties disclaim any duty whatsoever arising out of the assignment, withdrawal or suspension of an acknowledgment as well as any liability for any damage alleged to have been suffered on account thereof.
Credit-related and other analyses, including ratings, and statements in the Content are statements of opinion as of the date they are expressed and not statements of fact. S&P’s opinions, analyses and rating acknowledgment decisions (described below) are not recommendations to purchase, hold, or sell any securities or to make any investment decisions, and do not address the suitability of any security. S&P assumes no obligation to update the Content following publication in any form or format. The Content should not be relied on and is not a substitute for the skill, judgment and experience of the user, its management, employees, advisors and/or clients when making investment and other business decisions. S&P does not act as a fiduciary or an investment advisor except where registered as such. While S&P has obtained information from sources it believes to be reliable, S&P does not perform an audit and undertakes no duty of due diligence or independent verification of any information it receives. Rating-related publications may be published for a variety of reasons that are not necessarily dependent on action by rating committees, including, but not limited to, the publication of a periodic update on a credit rating and related analyses.
No content (including ratings, credit-related analyses and data, valuations, model, software or other application or output therefrom) or any part thereof (Content) may be modified, reverse engineered, reproduced or distributed in any form by any means, or stored in a database or retrieval system, without the prior written permission of Standard & Poor’s Financial Services LLC or its affiliates (collectively, S&P). The Content shall not be used for any unlawful or unauthorized purposes. S&P and any third-party providers, as well as their directors, officers, shareholders, employees or agents (collectively S&P Parties) do not guarantee the accuracy, completeness, timeliness or availability of the Content. S&P Parties are not responsible for any errors or omissions (negligent or otherwise), regardless of the cause, for the results obtained from the use of the Content, or for the security or maintenance of any data input by the user. The Content is provided on an “as is” basis. S&P PARTIES DISCLAIM ANY AND ALL EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, ANY WARRANTIES OF
MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE OR USE, FREEDOM FROM BUGS, SOFTWARE ERRORS OR DEFECTS, THAT
THE CONTENT’S FUNCTIONING WILL BE UNINTERRUPTED OR THAT THE CONTENT WILL OPERATE WITH ANY SOFTWARE OR HARDWARE
CONFIGURATION. In no event shall S&P Parties be liable to any party for any direct, indirect, incidental, exemplary, compensatory, punitive, special or consequential damages, costs, expenses, legal fees, or losses (including, without limitation, lost income or lost profits and opportunity costs or losses caused by negligence) in connection with any use of the Content even if advised of the possibility of such damages.



















