
Dubai, United Arab Emirates: Since 2020, Forescout Research - Vedere Labs has been tracking the riskiest devices on organizations’ networks. In 2020, the company released the first Enterprise of Things Security Report, followed in 2022 with the Riskiest Connected Devices in Enterprise Networks report.
Forescout’s reports are entirely based on data coming directly from connected devices. Throughout the years, Forescout has noticed that although many device types are consistently in these lists – such as IP cameras, VoIP equipment and programmable logic controllers (PLCs) – due either to their inherent criticality or to the persistent lack of attention from security teams – there are other devices whose current risk level reflects developments in the threat landscape.
For instance, in 2022 Forescout reported on hypervisors becoming a major target for ransomware – which is a trend that only grew and continued into 2023. However, the dataset in Forescout’s 2022 report (January through April) did not include several important later developments that knocked hypervisors off the list, such as the increased targeting of unmanaged devices by hacktivists, growing numbers of employees returning to their offices after the COVID-19 pandemic and intensified attacks against Western critical infrastructure following the Russian invasion of Ukraine.
In its latest report, Forescout presents its findings about the riskiest devices in enterprise networks for 2023. Forescout again takes a data-driven approach by analyzing millions of devices in Forescout’s Device Cloud using Forescout’s multifactor risk scoring methodology, detailed in the report.
What are the riskiest connected devices in 2023?
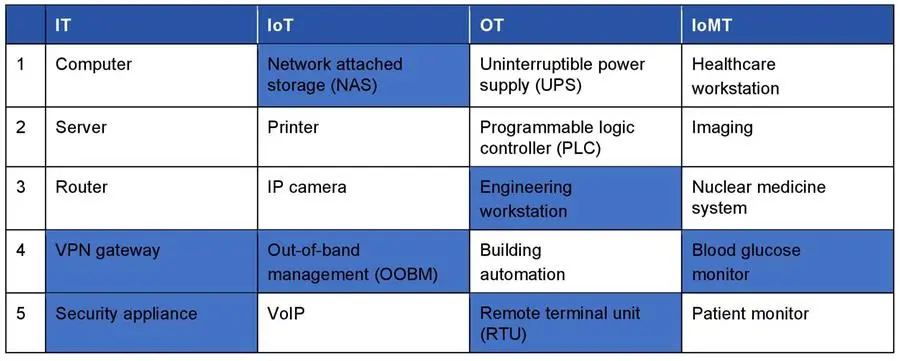
Using the dataset and scoring methodology described above, Forescout identified the five riskiest device types in four device categories: IT, IoT, OT and IoMT, for a total of 20 device types.
IT: Computer, Server, Router, VPN gateway, Security appliance
IoT: Network attached storage (NAS), Printer, IP camera, Out-of-band management (OOBM), VoIP
OT: Uninterruptible power supply (UPS), Programmable logic controller (PLC), Engineering workstation, Building automation, Remote terminal unit (RTU)
IoMT: Healthcare workstation, Imaging, Nuclear medicine system, Blood glucose monitor, Patient monitor
Among these 20 connected device types:
- 13 were already discussed in the 2022 report and remain on the list: computers, servers and routers in IT; printers, IP cameras and VoIP in IoT; UPS, PLCs and building automation in OT; healthcare workstations, imaging devices, nuclear medicine and patient monitors in IoMT.
- Seven device types are new to the list: VPN gateways and security appliances in IT; NAS and OOBM in IoT; engineering workstations and RTUs in OT; and blood glucose monitors in IoMT
2023 riskiest connected devices: key findings
- More than 4,000 vulnerabilities affect the devices in Forescout dataset. Out of those, 78% affect IT devices, 14% affect IoT, 6% affect OT and 2% affect IoMT. Although most vulnerabilities affect IT devices, almost 80% of them have only high severity. In contrast, IoMT devices have fewer vulnerabilities, but 80% of them are critical, which typically allows for complete takeover of a device. Similarly, more than half of the vulnerabilities affecting OT and IoT devices are critical.
- In all industries, at least 10% of devices that have endpoint protection installed have it disabled. This figure is highest in government and financial services (both with almost 24%), followed closely by healthcare (21%).
- Healthcare is the riskiest industry in 2023, followed by retail and manufacturing. Devices in healthcare are more likely to have dangerous ports, such as Telnet, SSH and RDP open. Almost 10% of devices in healthcare still have Telnet ports open, compared to 3-4% of devices in other verticals.
- The highest risk reduction Forescout observed from 2022 to 2023 was in government. However, indicators of compromise (IOCs), such as known malicious IPs and domains, were detected most often in government (63% of IoCs), followed by healthcare (19%) and financial services (8%).
- IT network infrastructure and security appliances are the most exposed devices on the internet. They are followed by IoT devices such as IP cameras (an overwhelming majority of IoT at 23%), NAS (7%) and VoIP (3%). There are also large numbers of exposed office equipment such as printers and NAS in government (19%) and OT in financial services (6%, mostly UPS).
- Traditional operating systems such as Windows and Linux are the majority in every industry, but special purpose operating systems, such as embedded firmware, are particularly strong in retail (14%), healthcare (13%) and government (12%). Managing unsupported legacy versions, tracking the variety of special purpose OSes and dealing with the systematic security issues in embedded firmware are nightmares for security teams.
- Specialized devices run legacy Windows much more frequently than general-purpose IT devices. For example, 63% of OT devices and 35% of IoMT devices that run Windows are on legacy versions of the OS. This is because of their long lifespans, the legacy applications they run and the need for vendors to certify that they can be safely upgraded to newer OSes.
Beyond the rankings: how to protect your attack surface
Risk is not only about the likelihood of being attacked, but also considers impact factors such as business criticality. Therefore, the list of riskiest devices does not always perfectly align with the most attacked devices. Nevertheless, Forescout does expect that several of the riskiest devices it identified will be among the most attacked in 2023. Especially the IT network infrastructure devices (routers, security appliances and VPN gateways) and the NAS in IoT show signs of only becoming more popular with attackers.
Some of Forescout’s findings point to specific actions you can take to reduce immediate risk:
- Prevalence of legacy Windows and critical vulnerabilities in OT and IoMT – Upgrade, replace or isolate these devices as much as possible.
- Often-disabled endpoint protection solutions in IT devices – Adopt automated device compliance verification and enforcement to ensure that noncompliant devices cannot connect to the network.
- Commonly found exposed devices such as IP cameras and dangerous open ports such as Telnet – Improve network security efforts, including segmentation.
Beyond these specific recommendations, the increased risk profiles of devices as diverse as security appliances, VPN gateways, NAS, OOBM and blood glucose monitors means that organizations need to embrace the fact that today’s evolving threat landscape requires new, superior security approaches to identify and reduce risk.
To bypass traditional endpoint security approaches, threat actors are consistently moving to devices that offer easier initial access. Modern risk and exposure management must encompass devices in every category to reduce risk across the whole organization. Solutions that work only for specific devices cannot effectively reduce risk because they are blind to other parts of the network being leveraged for an attack. For instance, OT- or IoMT-only solutions cannot assess risk for IT devices, while IT-only solutions will miss the nuances of the specialized devices.
Beyond risk assessment, risk mitigation should use automated controls that do not rely only on security agents. Likewise, they must apply to the whole enterprise instead of silos like the IT network, the OT network or specific types of IoT devices.
CTA
Understand what makes the riskiest connected devices so risky. Then strive for full visibility into how many are connecting to your environment so you can secure your attack surface.
-Ends-
Please follow the link to download the word version, full report and images: https://we.tl/t-ZLh4dBSoWd
About Forescout
Forescout Technologies, Inc. delivers automated cybersecurity across the digital terrain, maintaining continuous alignment of customers’ security frameworks with their digital realities, including all asset types- IT, IoT, OT, IoMT, and cloud environments. The Forescout Platform provides complete asset visibility, continuous compliance, network segmentation and a strong foundation for Zero Trust. For more than 20 years, Fortune 100 organizations and government agencies have trusted Forescout to provide automated cybersecurity at scale. Forescout arms customers with data-powered intelligence to accurately detect risks and quickly remediate cyberthreats without disruption of critical business assets. www.forescout.com
Managing cyber risk, together.



















