
Dubai: Western Digital thanked Positive Technologies expert Nikita Abramov for detecting a vulnerability in the firmware of Western Digital's network attached storage devices. The vulnerability could lead to remote execution of arbitrary code on the storage devices, data loss, and breach of confidential information. The vendor was notified of the threat as part of the responsible disclosure policy and subsequently released patches to fix the issues.
At the time of writing, IP addresses of 67 of Western Digital's network-attached storage devices in the Middle East were still available on the global network.
The CVE-2023-22815 vulnerability (scored 8.8 on the CVSS 3.0 scale) was detected in the firmware of My Cloud OS 5, v5.23.114. This software is used in several Western Digital's network devices: My Cloud PR2100, My Cloud PR4100, My Cloud EX4100, My Cloud EX2 Ultra, My Cloud Mirror G2, and others.
Nikita Abramov, Specialist of the Security Weakness Advanced Research and Modeling Center (PT SWARM)[1], commented: "The most dangerous scenario is a complete seizure of control over NAS (network attached storage, a file storage server). All further steps depend on the attacker's objectives: stealing, modifying, or completely removing data, and possibly deploying malware. The vulnerability is likely caused by adding new functionality to NAS without proper security checks. Other similar parts of the web interface (that could be used for command injection) filtered and checked the received data, preventing cyberattacks from happening."
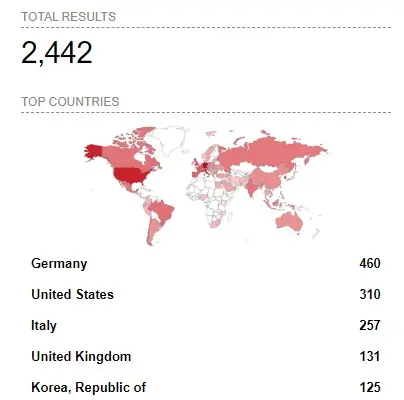
At the time of writing, IP addresses of more than 2,400 of Western Digital's network-attached storage devices were available on the global network. Most of them were in Germany (460), the United States (310), Italy (257), the UK (131), and South Korea (125).
Western Digital recommends installing the updated My Cloud OS 5 v5.26.300 firmware on all affected devices. For a complete list of these devices, see the vendor's advisory summary.
Positive Technologies recommends that companies build vulnerability management processes. It is necessary to regularly update software in use, carefully monitor a company's crucial assets, and focus on trending vulnerabilities first.
In 2022, PT SWARM helped eliminate 85 critical vulnerabilities in products of the largest manufacturers used in numerous industries all over the world.
-Ends-
About:
Positive Technologies is an industry leader in results-oriented cybersecurity and a major global provider of information security solutions. Our mission is to safeguard businesses and entire industries against cyberattacks and non-tolerable damage. Over 3,300 organizations worldwide use technologies and services developed by our company. Positive Technologies is the first and only cybersecurity company in Russia to have gone public on the Moscow Exchange (MOEX: POSI), with 170,000 shareholders and counting. Follow us in the News section at ptsecurity.com
1 PT SWARM is a team of 60 offensive security experts who carry out penetration tests (including red teaming), analyze the security of applications (mobile and web applications, as well as applications for the financial industry), analyze systems using social engineering, and audit wireless networks, ATMs, and POS terminals. On average, the team successfully completes over 100 projects annually.
PRESS OFFICE
ptsecurity.com,pr@ptsecurity.com
vk.com/ptsecurity, t.me/Positive_Technologies, twitter.com/ptsecurity, vk.com/phdays



















